Threat Response - Integration with ArcSight¶
The ArcSight SIEM platform serves as a log repository and allows administrator’s to build correlation rules to generate alerts when suspicious activity is detected in the logs. These alerts can be forwarded to Threat Response, and managed through the Threat Response incident management workflow. This document covers all aspects of Threat Response integration with HP ArcSight Enterprise Security Manager (ESM).
1. Forwarding Alerts to Threat Response¶
The steps below detail the process for creating an ArcSight alert source in Threat Response. Once configured, ArcSight will begin sending syslog alerts to Threat Response to generate incidents in the Threat Response platform.
Note
ArcSight utilizes a purpose-built FLEX Connector to relay alerts to Threat Response. In order to use this connector, you must have HP’s SmartConnector service running on a Linux host. Please refer to HP’s website for details regarding the installation of the SmartConnector service.
Creating an Alert Source in Threat Response¶
You must first create an alert source in Threat Response to receive alerts from ArcSight.
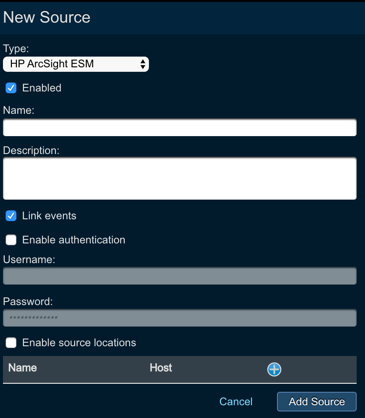
- Log in to Threat Response
- Navigate to the
Sourcespage - Click the blue
Add (+)button next toSourcesto bring up theNew Source panel - Set the following fields:
- Type: HP ArcSight ESM
- Enabled: enable the alert source after configuration is saved
- Name: provide the name of the alert source
- Description: provide the description for the alert source
- Link Events: let Threat Response to automatically group events under the incident
- Authentication: you can also enable authentication by providing username and password
- Enable Source Locations: you can limit the source location by IP address/host. Clicking on the + icon you can provide the name and the hostname for the alert source that you want to communicate with Threat Response. If you do so, other alert sources of the similar types will be ignored.
Savechanges.
Note
Make note of the POST URL for this alert source, as this will be required in the next section. The POST URL can be found in the Details panel for your newly created ArcSight source.
2. Unpacking the Threat Response FLEX Connector¶
Next, you will need to unpack the Threat Response FLEX Connector package. This should be done on the Linux system running HP’s SmartConnector service.
- Copy PTR_ArcSight_Connector.zip to the system running SmartConnector.
- Unpack the archive.
unzip PTR_ArcSight_Connector-<version>.zip- Make the following changes to
threatresponse.counteract.properties:- Update the last line,
command[0].action, to reflect the following path:ArcSight_Home/bin/threatresponse_counteract_command.sh
- Update the last line,
Note
ArcSight_Home represents the root installation directory for the SmartConnector service.
- Make the following changes to
threatresponse_counteract_command.sh:- Update the
POST_URLSvariable to reflect the POST URL for your ArcSight alert source in Threat Response. - If using the default SSL certificate on Threat Response, change
CURL="/usr/bin/curl"toCURL="/usr/bin/curl -k".
- Update the
Note
The “-k” disables certificate verification. Once a CA-signed certificate is installed on Threat Response, the “-k” should be removed.
- Move the modified files to the following locations:
mv threatresponse.counteract.properties <ArcSight_Home>/user/agent/flexagent/
mv threatresponse_counteract_command.sh <ArcSight_Home>/bin/3. Running the ArcSight SmartConnector setup script¶
Once the Threat Response FLEX Connector is unpacked and installed, you will need to run the SmartConnector setup script to configure the connector.
- Change directories, and run the SmartConnector setup script to configure the Threat Response FLEX Connector.
cd ArcSight_Home/bin
./runagentsetup.sh- Set the following options during the setup:
- What to do:
Add a connector - Select the connector to configure:
ArcSight FlexConnector CounterACT - Enter the parameter details:
threatresponse. The setup script will append “.counteract.properties” to reference the configuration file unpacked in Step 1. - Enter the type of destination:
ArcSight Manager - Enter the destination parameters using the following values:
- Manager Hostname:
hostname - Manager Port:
port - User:
username - Password:
password - AUP Master Destination:
False - Filter Out All Events:
False - Enable Demo CA:
yes/no
- Manager Hostname:
- Enter the connector details using the following values:
- Name:
connector_name - Location:
location_in_arcsight_console - DeviceLocation:
device_location - Comment:
comment
- Name:
- Install as a service:
Yes - Specify the service parameters using the following values:
- Service Internal Name:
choose_service_name - Service Display Name:
choose_service_display_name - Start the service automatically:
Yes
- Service Internal Name:
- What to do:
- Following the connector setup, select Exit to leave the script.
4. Starting the Threat Response FLEX Connector¶
Start the connector service with the following command:
/etc/init.d/service_name start5. Verifying the Connector is Functional¶
Now is a good time to verify that ArcSight ESM detects the connector, and to push a test alert through to confirm end-to-end communication between ArcSight ESM and Threat Response.
Use the steps below to confirm connector functionality:
- Log in to the ArcSight Console.
- Select Connectors from the ArcSight Console Navigator (left panel).
- Verify that the connector you installed appears in your connectors list and is marked as (running).
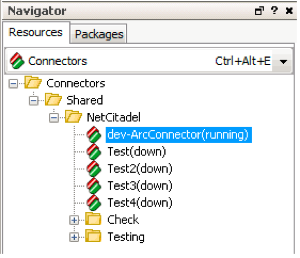
- Test the connector by right-clicking on it and selecting
Send Command>CounterACT>Send to Threat Response.
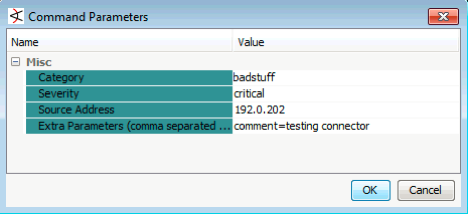
ArcSight Console will pop up a window where you can manually supply alert details as seen above. Fill out these details and click OK to execute the connector command. This will push a test alert into the Threat Response appliance.
6. Configuring a Rule to Use the Connector¶
Finally, rules can be configured to use the connector to forward alerts to Threat Response. The steps below detail the configuration of a single rule.
- Log in to the ArcSight Console.
- Select
Rulesfrom theArcSight Console Navigator(left panel). - Select the rule that you want to forward to Threat Response.
- In the
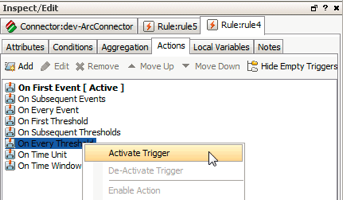
Rule Inspector, click on theActionstab. - Right-click
On Every Thresholdand selectActivate Triggerto generate an alert each time the rule threshold is reached.
Note
On Every Threshold will now appear in bold font to indicate that it is active.
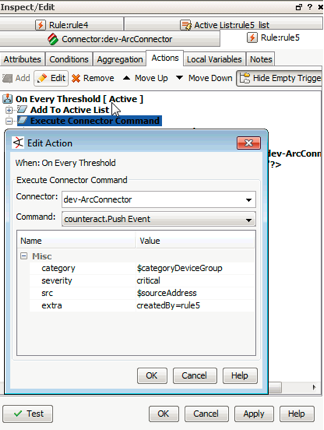
- Right-click
On Every Thresholdagain and selectExecute Connector Command.- An
Edit Actionpopup will appear. - Update the action to map the appropriate event variables to the fields defined in the connector.
- Click
OK.
- An
Applyyour changes.