Threat Response - Integration with Fortigate¶
This document covers all aspects of Threat Response integration with Fortinet FortiGate firewalls. The Proofpoint Threat Response platform can integrate with the FortiGate line in the following ways:
- As an Enforcement Device
Fortinet FortiGate can be used to prevent network-based access to malicious hosts, or to restrict access to certain areas of the network for infected users. Threat Response can place suspicious hosts reported in security alerts into a Threat Response block list, which is then pushed up to the FortiGate as an address group to be used when building policies.
Configuring a Fortinet FortiGate Device¶
The steps below detail the process for configuring Threat Response to map a local block list to an address group in a Fortinet FortiGate device. With the mapping in place, policies can be created on the FortiGate that reference the address group managed by Threat Response.
Create a Host List in Threat Response¶
The first step in enabling synchronization with Fortinet FortiGate is to create a Host List in Threat Response to map to an address group on the FortiGate. Follow the steps below to create the Host List in Threat Response.
- Log in to Threat Response.
- Navigate to the
Listspage. - Click on the
Host Listssub-tab to manage yourURL Lists. - Click the blue
Add (+)button next toListsto bring up theNew Host Listpanel. - Set the following fields:
- Name:
<list_name> - Description:
<list_description>(Optional) - Publish:
<checked_or_unchecked>(Optional)
- Name:
- Save changes.
Note
List Publishing enables remote polling of a list in Threat Response via HTTP/S. It is not required for a Fortinet FortiGate configuration.
Create a FortiGate Device¶
In order to map a Threat Response list to your Fortinet FortiGate device, you must first tell Threat Response how to communicate with that device.
- Log in to Threat Response
- Navigate to the
Devicespage - Click on the
Network Devicessub-tab - Click the blue
Add (+)button next toNetwork Devices to bring up theNew Network Devicepanel
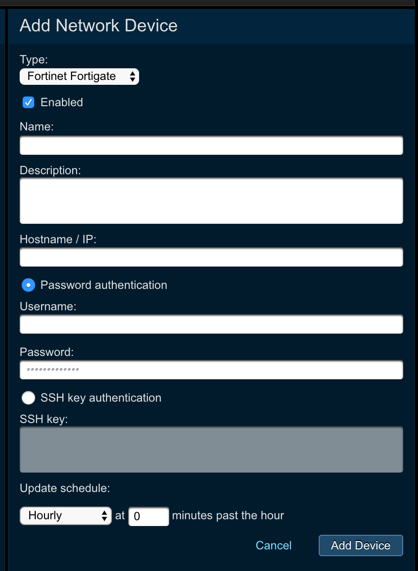
- Set the following fields:
- Enabled: enable the device after the configuration is saved
- Name: provide device name
- Description: provide device description
- Hostname / IP: provide IP or hostname of the device
- Authentication: you can choose between password authentication, where you need to provide username and password, or SSH key authentication, where you need to upload the SSH key to Threat Response
- Update this device: Define the update schedule by choosing the appropriate option from the drop down menu
Savechanges.
Map a List to the FortiGate Device¶
Once your Fortinet FortiGate device has been created in Threat Response, you can begin mapping lists to it. These will appear as address groups in the FortiGate.
Note
Once saved, Threat Response will automatically connect to the FortiGate, and attempt to create the group on the device. If the group already exists, it will be overwritten with the items in the Threat Response list.
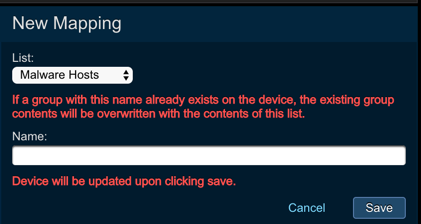
To map a list to a Fortinet FortiGate device:
- Log in to Threat Response.
- Navigate to the
Devicespage. - Click on the
Fortinet FortiGatedevice that you want to map a list to. - In the
Device Detailspanel, click the blueAdd (+)button next toList Mappingsto open theNew Device Mappingpanel. - Select the appropriate list from the
Listdropdown. - Input a
Group Nameto tell Threat Response what to name the address group in the Fortinet FortiGate. Savechanges.