Threat Response - Integration with Splunk Enterprise v1.0¶
This document covers all aspects of Threat Response integration with Splunk Enterprise. Today Threat Response can integrate with Splunk Enterprise in two ways: Splunk Alert Source, and Splunk Log Source. We will explore the specifics of these integrations in this integration guide.
Note
This integration guide covers legacy integration capabilities using Splunk RSS feeds, and for this integration the Splunk Enterprise 1.0 Alert Source is used. It is recommended that you use Splunk Alert Source 2.0 and follow the following integration guide: Threat Response - Integration with Splunk Enterprise v2.0
| Type | Description | Versions |
|---|---|---|
| Splunk Alert source | Splunk Enterprise provides administrators the ability to define log-correlation rules that will detect anomalous or suspicious behaviors in the network. Upon detecting such an event, Splunk Enterprise can generate an alert to Threat Response for further investigation. | Splunk Enterprise 1.0 |
| Splunk Log Source | Threat Response can utilize Splunk Enterprise as a data repository to look for logs associated with bad actors (hackers) or infected machines. The ability to review logs for an infected machine may lead to further insights about what has changed on that machine, and what it is communicating to on the network. | N/A |
Configuring Splunk Enterprise Alert Source¶
Splunk Enterprise 1.0¶
The steps below detail the process for creating a Splunk Enterprise alert source in Threat Response. Once configured, Splunk rules can be built to send events to Threat Response to generate incidents in the Threat Response platform.
Create Splunk Enterprise 1.0 Alert Source in Threat Response¶
You must first create an alert source in Threat Response to receive alerts from Splunk.
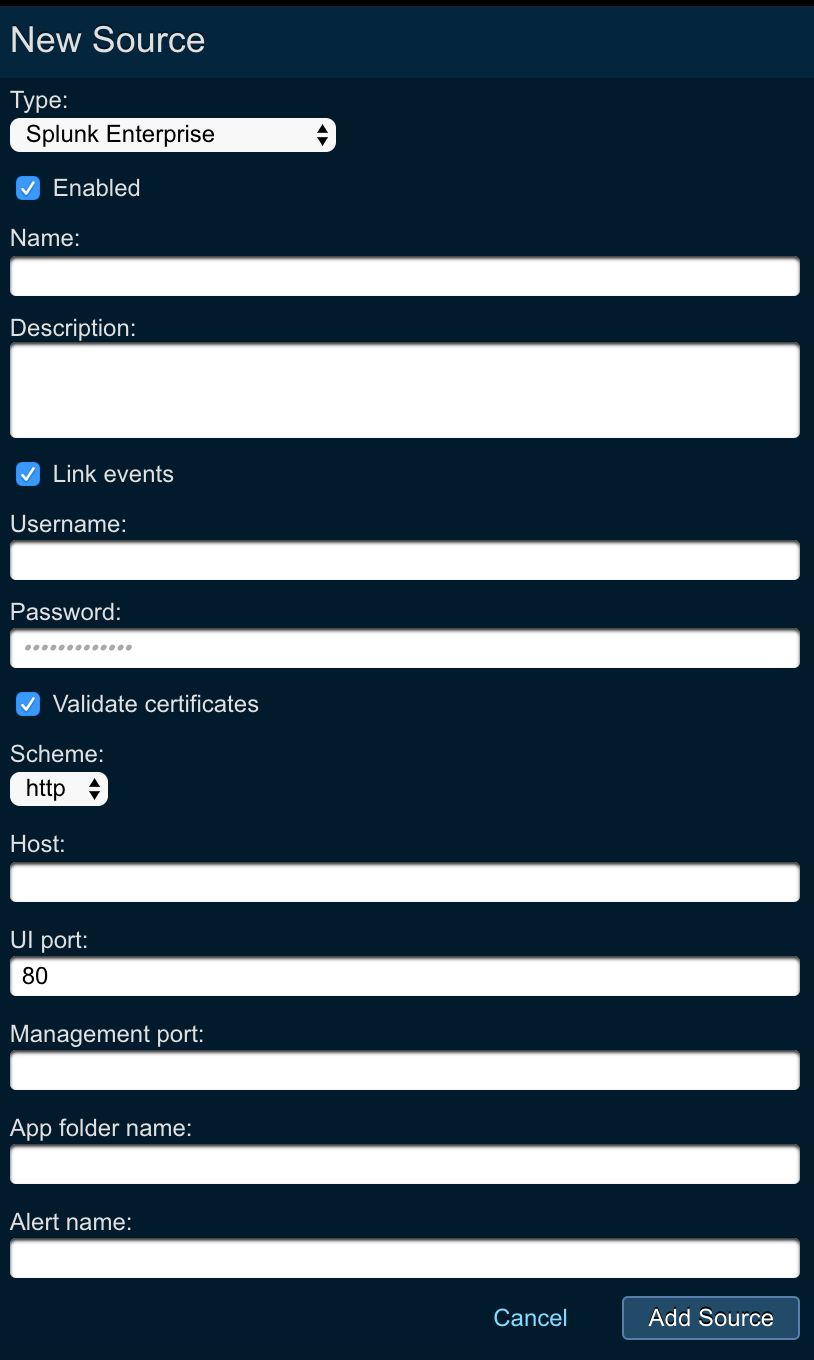
- Log in to Threat Response
- Navigate to the
Sourcespage - Click the blue
Add (+)button next toSourcesto bring up theNew Sourcepanel. - Set the following fields:
- Type:
Splunk Enterprise - Name:
<event_source_name> - Description:
<description> - Link Events:
<checked> - Username:
<splunk_username> - Password:
<splunk_password> - Scheme:
http -or- https - Host:
<splunk_hostname> - UI Port:
<splunk_ui_port> - Management Port:
<splunk_mgmt_port>(this is usually “8089”) - App Folder Name:
Search - Alert Name: Proofpoint Threat Response Alerts
- Type:
Savechanges.
Prepare Splunk to Process Alerts for Threat Response¶
As a next step, you will need to prepare Splunk to generate, and relay events to Threat Response. To do this, an event-generating script will be copied to Splunk, and special rule will be created to aggregate the Threat Response alerts into a single RSS feed.
- Login to Splunk Enterprise
- Navigate to
Settings>Data Inputs - Create a new Local Input with the following settings:
- Transport:
UDP - Port:
514 - Source name override:
Proofpoint Threat Response - Only accept connections from:
127.0.0.1 - Sourcetype:
Proofpoint Threat Response - App context:
Search & Reporting - Host:
IP - Index:
Default
- Transport:
- Navigate to
Settings>Searches, reports, and alerts - Create a new search rule to look for “Proofpoint Threat Response” alerts:
- Destination App:
Search & Reporting - Search Name: Proofpoint Threat Response Alerts
- Search: source=”Proofpoint Threat Response”
- Description: Query designed to aggregate security alerts into one RSS feed for Proofpoint Threat Response
- Start time:
rt - Finish time:
rt - Schedule and alert:
checked - Alert Condition:
always - Alert Mode:
Once per result - Alert Actions:
Add to RSS
- Destination App:
Savethe new rule.- Copy
proofpoint_threat_response.pyto scripts directory in Splunk
# scp proofpoint_threat_response.py root@splunk:/opt/splunk/bin/scriptsNote
The script sample is available in the Appendix section: Splunk Enterprise 1.0 Python Script
Create Field Extractions to Parse Information from Logs¶
Field Extractions must be created to parse information from the raw logs received by Splunk. These field extractions will populate the Threat Response alert with data.
Note
You will need to create field extractions for each log type that you want to forward to Threat Response. This process is highly variable by sourcetype, thus it is recommended to use Splunk’s Field Extractor to accomplish this task. Please refer to Splunk’s documentation for more information on how to use the Field Extractor.
For Splunk Enterprise alert source Threat Response will recognize the following fields:
- description – a description of the event
- src_host – the source host
- src_port – the source port
- dst_host – the destination host
- dst_port – the destination port
- transport_protocol – the transport protocol used for network traffic
- result – the action performed by the reporting device: permitted, blocked, etc.
To configure Field Extractions:
- Log in to Splunk Enterprise
- Navigate to
Settings>Fields - Click on
Field Extractions - Click the
Open Field Extractorbutton - Select the sourcetype that you would like to extract data from
- Create extractions
Note
Sample field extraction are provided in the Appendix: Sample Field Extractions
Configure Splunk Rules to Forward Alerts to Threat Response¶
With all of the preparations in place, you can now begin updating existing Splunk rules, or creating new ones, to be sent to Threat Response. Note that this is the point where you can assign a category to your alerts, as well as “target” and “attacker” roles to IPs or hostnames extracted from the logs.
Supported alert categories:
- malware – Malware alerts
- command-and-control – Command & control activity related to malware
- vulnerability – General vulnerabilities (system or network)
- network – Network-based attacks
- data-match – Data-pattern matching, DLP
- policy-violation – General policy violations
- system-behavior – Suspicious endpoint behaviors
- authentication – Authentication attacks, brute-force, etc.
To configure Splunk rules:
- Log in to Splunk Enterprise
- Navigate to
Settings>Searches, reports, and alerts - Click to open an existing rule to be forwarded to Threat Response
- Update search pattern to pull out necessary fields
… | fields src_host, src_port, dst_host, dst_port, transport_protocol, result, description- Update search pattern to set the category of the alert
… | setfields alert_category="network"- Update search pattern to assign attacker / target roles to hosts
… | eval attack_host=src_host | eval target_host=dst_host | eval attack_port=coalesce(src_port, "") | eval target_port=coalesce(dst_port, "")- In the Alert section, enable the following:
- Alert actions: Run a script
- File name of shell script to run:
proofpoint_threat_response.py
Savechanges
Configuring Splunk Log Query¶
Splunk logs can be viewed directly in Threat Response for hosts reported in incidents. Once you have enabled the Splunk Log Query feature, you will be able to view logs associated with a host by opening an incident, and navigating to the IP Details page.
Build Splunk Search Query¶
The first step is to consider the search query that you want to use to locate logs in Splunk. This query will be used in the next step when configuring the feature. The query syntax is exactly the same as queries performed directly in Splunk; however, the string you are searching is represented by the variable “{entity}” (without the quotes).
Below is a sample query that will search for the current {entity}, will exclude any Threat Response alerts generated for the event source, and will limit the results to 100 entries:
search {entity} NOT sourcetype="Proofpoint Threat Response" | head 100This query is recommended for most installations.
Note
You should always apply a result limiter to the query. Large numbers of results will result in slow load times on Threat Response, and may create unnecessary load on the Splunk server.
Enable Log Query¶
With Splunk Log Query enabled on Threat Response, you can navigate to the IP Details tab in any incident to view logs associated with a host. When the page is loaded, Threat Response will begin the query to Splunk to collect the logs, and will display a count of the logs that were found. Clicking on the count will display a popup containing the raw logs.
To enable SIEM Log Collection for Splunk:
- Log in to Threat Response.
- Navigate to
System Settings>Contextual Data Sources>Splunk. - Check the box to enable Splunk Integration and configure the following:
- Host:
<Splunk hostname_or_ip> - Management Port:
<splunk_mgmt_port>(this is usually “8089”) - UI Port:
<splunk_ui_port> - Username:
<splunk_username> - Password:
<splunk_password> - Use SSL: (optional)
- Default Query:
<custom_splunk_search_query>
- Host:
- Optionally, click on
“Test Settings”button to verify that the Splunk instance is reachable. Savechanges.
Appendix¶
This section contains samples that can be used as a reference point when configuring Splunk Enterprise to work with Threat Response.
Sample Field Extractions¶
Cisco IOS (access-list logs)
* description - (?i)%(SYS|SEC)-\d-[^:]+: (?P<description>.+)
* dst_host - (?i)^[^>]*>\s+(?P<dst_host>[^\s\(]+)
* dst_port - (?i)^(?:[^\(]*\(){3}(?P<dst_port>[^\)]+)
* result - (?i)(?P<result>[^ ]+) (icmp|udp|tcp)
* src_host - (?i) (icmp|udp|tcp) (?P<src_host>[^\s\(]+)
* src_port - (?i)^(?:[^\.]*\.){7}\d+\((?P<src_port>[^\)]+)
* transport_protocol - (?i) (permitted|denied) (?P<transport_protocol>[^ ]+)Windows Event Log (login events)
* description - (?i)^[^\]]*\]\s+\d+\s+(?P<description>[^\.]+)
* result - (?i)^[^\[]*\[(?P<result>[^\]]+)
* source_event_id - (?i)\[.*?\] (?P<source_event_id>\d+)(?= )
* src_host - (?i)Source Network Address:(?P<src_host>.+?)
* src_port - (?i)Source Port:(?P<src_port>.+?)
* account_name - (?i)Account Name:.*?Account Name:(?P<src_user>.+?)Sample Splunk Rules¶
Traffic to Dark Subnet
Description: Looks for any traffic going to 10.10.127.x (an unused subnet)
Search string:
sourcetype="cisco ios" dst_host=10.10.127.* | fields src_host, src_port, dst_host, dst_port, transport_protocol, action, description | setfields alert_category="network" | eval attack_host=src_host | eval target_host=dst_host | eval attack_port=coalesce(src_port, "") | eval target_port=coalesce(dst_port, "")Unauthorized SMTP Traffic
Description: SMTP traffic seen from non-SMTP hosts
Search string:
sourcetype="cisco ios" AND dst_port=25 NOT 10.10.10.2 | fields src_host, src_port, dst_host, dst_port, transport_protocol, action, description | setfields alert_category="network" | eval attack_host=src_host | eval target_host=dst_host | eval attack_port=coalesce(src_port, "") | eval target_port=coalesce(dst_port, "")Splunk Enterprise 1.0 Script¶
#!/opt/splunk/bin/python
#
# proofpoint_threat_response.py
#
# Copyright 2014 Proofpoint, Inc.
#
# Proofpoint Threat Response supports two modes of monitoring Splunk alerts
# with PTR Event Sources: one-to-one and one-to-many. This script facilitates
# the one-to-many case: you wish to monitor several Spunk alerts with a single
# PTR Event Source.
#
# This script should be run as the response action of every Splunk alert you
# want to consolidate for a single PTR Event Source. Every time the alert is
# triggered, it assembles a JSON representation and feeds it back into Splunk
# through a special Data Input, which you must configure. By defining a
# "meta-alert" for this Data Input and publishing an RSS feed, PTR can
# monitor an arbitrary number of Splunk alerts with a single Event Source.
#
# Troubleshooting:
# - The python path given in the first line must be the path to Splunk's
# python interpreter: $SPLUNK_HOME/bin/python.
# - This script must be placed in $SPLUNK_HOME/bin/scripts and must be
# marked as executable.
# - The PROOFPOINT_UDP_PORT variable must be set to the port number of a
# Splunk UDP Data Input, and it is recommended that this Data Input
# be configured with sourcetype='proofpoint_threat_response'.
#
import os
import sys
import csv
import gzip
import logging
import json
import time
import socket
# Set this to the port of a Splunk UDP Data Input, configured with
# sourcetype='proofpoint_threat_response'
PROOFPOINT_UDP_PORT = None
LOGNAME = 'proofpoint_threat_response.log'
# Uncomment this line to log script output to stderr
#LOGFILE = None
# Uncomment this line to log to the script's directory
LOGFILE = '%s/%s' % (os.path.dirname(os.path.realpath(sys.argv[0])), LOGNAME)
# Uncomment this line to log to /var/log/
#LOGFILE = '/var/log/%s' % LOGNAME
def configureLogging(alert_name):
LOG_FORMAT = '%(asctime)s, ' + alert_name + ', %(levelname)s: %(message)s'
if LOGFILE is not None:
logging.basicConfig(level=logging.INFO, format=LOG_FORMAT,
datefmt='%Y-%m-%d %H:%M%S', filename=LOGFILE)
else:
logging.basicConfig(level=logging.INFO, format=LOG_FORMAT,
datefmt='%Y-%m-%d %H:%M%S')
def parseFieldNames(names):
indicesToNames = {}
for idx, name in enumerate(names):
indicesToNames[idx] = name
return indicesToNames
def retrieveResults(filename):
logging.info('Retrieving events from %s...' % filename)
try:
events = []
# Splunk stores search results in gzipped csv files
with gzip.open(filename, 'rb') as eventFile:
eventReader = csv.reader(eventFile)
# The first line of the file contains the field names
indicesToNames = parseFieldNames(eventReader.next())
logging.info('Retrieved interesting fieldnames:')
logging.info(str(indicesToNames))
# Subsequent rows hold the data for each event in the alert
for row in eventReader:
event = {}
for idx, fieldname in indicesToNames.iteritems():
event[fieldname] = row[idx]
events.append(event)
logging.info('Successfully retrieved %d events' % len(events))
return events
except IOError as e:
logging.error('IOError retrieving events: %s. Exiting.' % e.strerror)
sys.exit(1)
def sendUDP(event_to_send, port):
logging.info('Sending the event via UDP to localhost:%d...' % port)
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
bytesToSend = len(bytearray(event_to_send, encoding='UTF-8'))
bytesSent = sock.sendto(event_to_send, ('localhost', port))
if bytesSent == bytesToSend:
logging.info('Successfully sent event to UDP port %d.' % port)
else:
logging.error('Only sent %d of %d bytes to UDP port %d. Event: %s' % (bytesSent, bytesToSend, port, event_to_send))
except IOError as e:
logging.error('IOError while sending to UDP port %d: %s', (port, e.strerror))
if __name__ == '__main__':
if PROOFPOINT_UDP_PORT is None:
logging.error('PROOFPOINT_UDP_PORT must be set')
sys.exit(1)
alert_name = os.environ['SPLUNK_ARG_4']
configureLogging(alert_name)
logging.info('---------------- Script started ----------------')
# Start building the event for Threat Response
tr_event = {}
tr_event['proofpoint_aggregate_alert'] = True
tr_event['alert_time_utc'] = time.strftime('%Y-%m-%dT%H:%M:%SZ', time.gmtime())
tr_event['alert_name'] = alert_name
tr_event['event_count'] = os.environ['SPLUNK_ARG_1']
tr_event['query_string'] = os.environ['SPLUNK_ARG_3']
tr_event['trigger_reason'] = os.environ['SPLUNK_ARG_5']
tr_event['browser_url'] = os.environ['SPLUNK_ARG_6']
# Retrieve the temporary file of raw search results and parse the data
filename = os.environ['SPLUNK_ARG_8']
logging.info('Retrieved raw results filename=%s' % filename)
tr_event['results_filename'] = filename
results = retrieveResults(filename)
tr_event['results'] = results
# Send the event back into Splunk via UDP
event_to_send = json.dumps(tr_event)
sendUDP(event_to_send, PROOFPOINT_UDP_PORT)
logging.info('Script finished.')