Threat Response - Installation Guide (AWS)¶
The Installation Guide (Amazon Web Services) is a step-by-step guide to setting up Threat Response and TRAP as an instance inside Amazon Web Services (AWS) Elastic Compute Cloud (EC2). Note that it is important that you use an AWS account that has been arranged by your organization to install PTR or TRAP.
Full documentation access
Threat Response documentation portal is accessible to Threat Response customers only. If you are accessing this page directly through the link, all the other content will be protected. To access all available documentation, please, perform the following steps:
1. Log in to Threat Response
2. At the top bar click on the ? link
3. You will be seamlessly redirected to the portal with full documentation access
Threat Response Requirements¶
Amazon Machine Image Requirements¶
Threat Response is a stand-alone virtual appliance. It is distributed as a VHDX file and requires that the file be imported into EC2. Note that the VHDX file can be downloaded from the Proofpoint customer portal. The recommended EC2 instance type is m5a.xlarge with the following configuration.
- 4x vCPU cores recommended (minimum: 2x vCPU Cores)
- 16 GB RAM recommended (minimum: 8 GB RAM)
- 50 GB HDD (base system for version 5.1 and beyond)
- 500 GB HDD (local databases and backups)
- 1 network adaptor
For administration and general usage, Threat Response will need one IP address allocated to it for network access.
Service accounts¶
Threat Response interfaces with other systems to receive alerts, perform user lookups, and update systems as part of its response capabilities. It is recommended, but not required, to use a service account for these interactions. Below is a list of systems and services that you may want to create a service account for.
- Event Sources (any detection systems where an API account is used)
- Enforcement Devices (firewalls and proxies)
- LDAP / Active Directory
- Read-only permissions required for user lookups
- Domain Admin permissions required for response behaviors (optional)
Note
For a trial run, any administrative-level account with read / write permissions will suffice in most cases.
Required Ports for Network Communication¶
Threat Response requires the following ports to be opened for management purposes, and to allow it to communicate with your devices. Refer to the table below for a list of ports that should be allowed between Threat Response and other systems.
| Port | Direction | Purpose |
|---|---|---|
| TCP/8080 | Admin Network to Threat Response | Appliance Management Console |
| UDP/514 | “Any” to Threat Response | To receive alerts sent via syslog |
| TCP/443 | “Any” (internal) to Threat Response | Threat Response GUI & HTTPS alert listeners |
| TCP/443 | Threat Response to “overcast.proofpoint.com” | Communication with Overcast for Alert Enrichment, Licensing and SmartSearch export from the Admin Portal |
| TCP/443 | Threat Response to “tap-api-v2.proofpoint.com” | Pulling alerts from TAP |
| TCP/443 | Threat Response to “saasisolation.com” and “proofpointisolation.com” | Rendering suspicious web pages from abuse-reported messages using Proofpoint Browser Isolation |
| TCP/443 | Threat Response to Exchange/O365/Gmail | Used to quarantine messages |
| TCP/443 | Threat Response to login.windows.net | Used to obtain OAuth token from Azure AD Auth for O365 connectivity |
| TCP/22 & TCP/443 | Threat Response to Network Devices | Used to push updates to Devices |
| TCP/22 | Admin Network to Threat Response | SSH access to CLI |
| UDP/137 | Threat Response to Endpoint PCs | Used to gather NetBIOS information from PCs |
| TCP/445 | Threat Response to Endpoint PCs | Used for PC Data Collection |
| TCP/7820 | Threat Response to Endpoint PCs | Used to communicate with the Remote Agent |
| TCP/389 | Threat Response to LDAP Server | Query LDAP for user details |
| TCP/636 | Threat Response to Secure LDAP Server | Query Secure LDAP for user details |
| TCP/25 | Threat Response to SMTP Server/Relay | Notifications & alerts via email |
| UDP/53 | Threat Response to DNS Server | DNS services |
| UDP/123 | Threat Response to NTP Server | NTP services |
Note that these ports must be configured in an AWS Security Group that is chosen specifically for your EC2 instance running Threat Response.
Note
Amazon EC2 instances do not have port TCP/25 open by default and thus email notification traffic is restricted from the PTR/TRAP appliance. You must create a support case with a formal request to AWS to remove this restriction from your instance. Refer to this AWS help article for detailed instructions on the process.
Domain Controller Agent requirements¶
In order to associate usernames to alerts as they are received, Threat Response must interface with a system that enables it to build a table of username-to-IP mappings. To do this, Threat Response employs a Domain Controller agent (DC Agent).
The DC Agent can be deployed in one of two ways:
- Directly on all Domain Controllers used for authentication
- A single instance can be deployed on a stand-alone Windows system to remotely query all Domain Controllers used for authentication
Domain Controller agent supports the following platforms:
| Platform | Version |
|---|---|
| Windows Server | Supported: 2008 (32-bit & 64-bit), 2012 (64-bit) |
Note
For detailed instructions on how to install and operate domain controller agent, please, refer to the following section Installing and configuring domain controller agent.
Supported browsers¶
Threat Response supports the following browsers:
| Browser | Version |
|---|---|
| Google Chrome | 51.0 + |
| Mozilla Firefox | 47.0 + |
Creating a Threat Response Instance from an Amazon Machine Image (AMI)¶
Configuring a Threat Response instance involves setting your system’s parameters. See the step-by-step instructions below. You can also refer to the official AWS VM Import/Export User Guide here.
Note
Certain of the steps below may require administrative or “privileged” access to your AWS account.
Prerequisites¶
This baseline information is a prerequisite for setting up an instance:
-
AWS Region Code: To select a region, click and expand the “region” field on the top right-hand corner of the AWS Console.
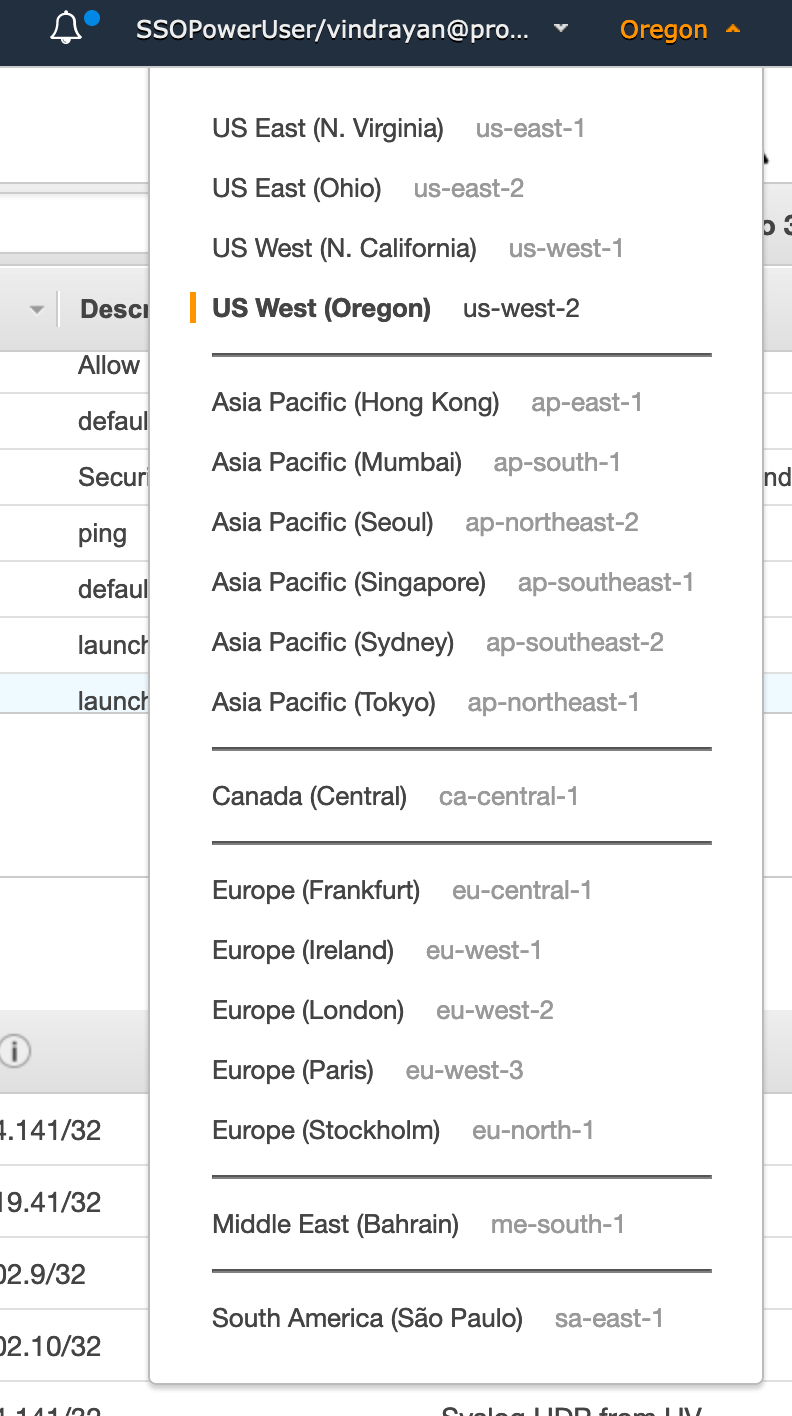
Be sure to make a note of it.
-
Identity and Access Management (IAM) Role (to Import Snapshot): Create an IAM role, namely vmimport, with a “trust relationship policy document,” to allow “VM Import” to assume the role. Note that you must attach the IAM policy to the role. Refer to the official AWS VM Import/Export User Guide for the specific requirements under Required Service Role.
-
AWS Access Key ID: To manage your Access Key ID, go to Services and then to the IAM column. Click on Users. Find and click on a user and then go to the Security Credentials tab. If no access key has been set up, click on Create Access Key to create a new key. Be sure to make a note of it at that time.
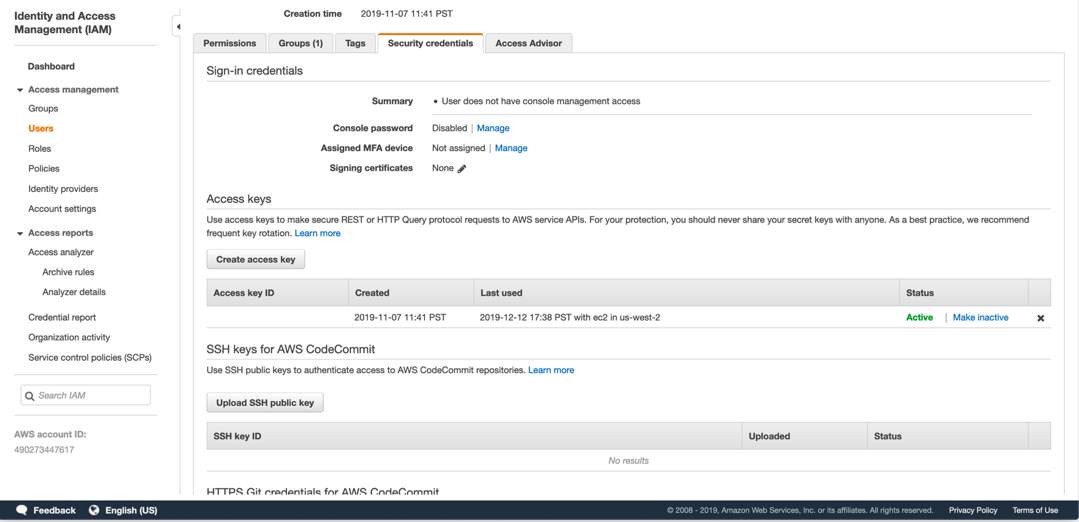
-
AWS Secret Access Key: The only way to see this key is when you create a new Access Key ID. (See above.) Be sure to make a note of it at that time.
Installing the AWS Command Line Interface (CLI) Version 1¶
Click this link for instructions.
Configuring the AWS CLI¶
Option 1: Run "AWS Configure."
$ aws configure
AWS Access Key ID [None]: YOUR_ACCESS_KEY_ID
AWS Secret Access Key [None]: YOUR_SECRET_ACCESS_KEY
Default region name [None]: YOUR_REGION_NAME
Default output format [None]: json
Option 2: Set the environment variables.
export AWS_ACCESS_KEY_ID=YOUR_ACCESS_KEY_ID
export AWS_SECRET_ACCESS_KEY=YOUR_SECRET_ACCESS_KEY
export AWS_DEFAULT_REGION=YOUR_REGION_NAME
export AWS_DEFAULT_OUTPUT=json
Run these commands on the command line or store them in your shell profile.Downloading the Threat Response VHDX File From Proofpoint¶
- Log on to Proofpoint Support (CTS) or Proofpoint Secure Share, as the case may be.
-
Download the VHDX file (4.5 GB):
Proofpoint_Threat_Response-5.1.1.vhdx.zipUnzip the file using a standard “zip” utility compatible with your desktop environment.
Note
The VHDX file must be within a file system location that is accessible via command line for the AWS CLI.
Copying the VHDX File to Amazon Simple Cloud Storage Service¶
- Decide on an Amazon S3 bucket in the same region as that which will be used for importing the VHDX file, e.g.
s3:/proofpoint/threatresponse -
Refer to the official AWS VM Import/Export User Guide for exporting an instance as a VM. (Search for Exporting an Instance as a VM Using VM Import/Export.) Importantly, be sure to attach an access-control list (ACL) to access your region-specific “import” account ID.
Moreover, verify that the appropriate EC2 and S3 bucket access policies are affixed to the vmimport role. The “role” must also have the applicable trust relationships to execute the import-snapshot command. Go to Trust Relationships and then to Edit Trust Relationships.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "ec2.amazonaws.com" }, "Action": "sts:AssumeRole" }, { "Effect": "Allow", "Principal": { "Service": "vmie.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
-
Run the following command using the AWS CLI.
aws s3 cp Proofpoint_Threat_Response-5.1.1.vhdx YOUR_S3_BUCKET_PATHFor Example
aws s3 cp Proofpoint_Threat_Response-5.1.1.vhdx.zip s3://proofpoint/threatresponse
Note
The copy operation can take a few minutes depending on the speed of the network connection.
Creating an Amazon Elastic Compute Cloud Snapshot File¶
Once the VHDX file has been copied to Amazon S3, it must be converted into a snapshot in Amazon EC2. The details of the VHDX file must be specified by means of a JSON object when creating the snapshot.
-
Create a file named THREATRESPONSE-VHDX.JSON containing the following data.
{ "Description": "YOUR_DESCRIPTION", "Format": "VHDX", "UserBucket": { "S3Bucket": "YOUR_S3_BUCKET_NAME", "S3Key": "S3_PATH_TO_VHDX_FILE" } } Example { "Description": "Threat Response 5.1", "Format": "VHDX", "UserBucket": { "S3Bucket": "proofpoint", "S3Key": "threatresponse/Proofpoint_Threat_Response-5.1.1.vhdx" } } -
Run the following command (using the AWS CLI) to create the snapshot.
`aws ec2 import-snapshot --description "threatresponse-snapshot-import" --disk-container "file://PATH_TO_THREATRESPONSE-VHDX.JSON"`
Note
The snapshot operation can take more than fifteen minutes. You can monitor its progress using the AWS CLI.
The above command returns JSON output with details of the operation, namely Progress (percentage), StatusMessage, ImportTaskId (import-snap-xxxxx), and SnapshotId (snap-xxxxx) (of the completed operation).
Monitoring the operation’s progress can be accomplished by running the following command.
aws ec2 describe-import-snapshot-tasks --import-task-ids import-snap-xxxxx
Creating an Instance From an Amazon Machine Image (Snapshot File)¶
- Proceed to Services and then go to EC2 in the AWS Management Console.
- Search for the snapshot by means of the SnapshotId. (See above.)
-
Right click the snapshot and then select Create Image.
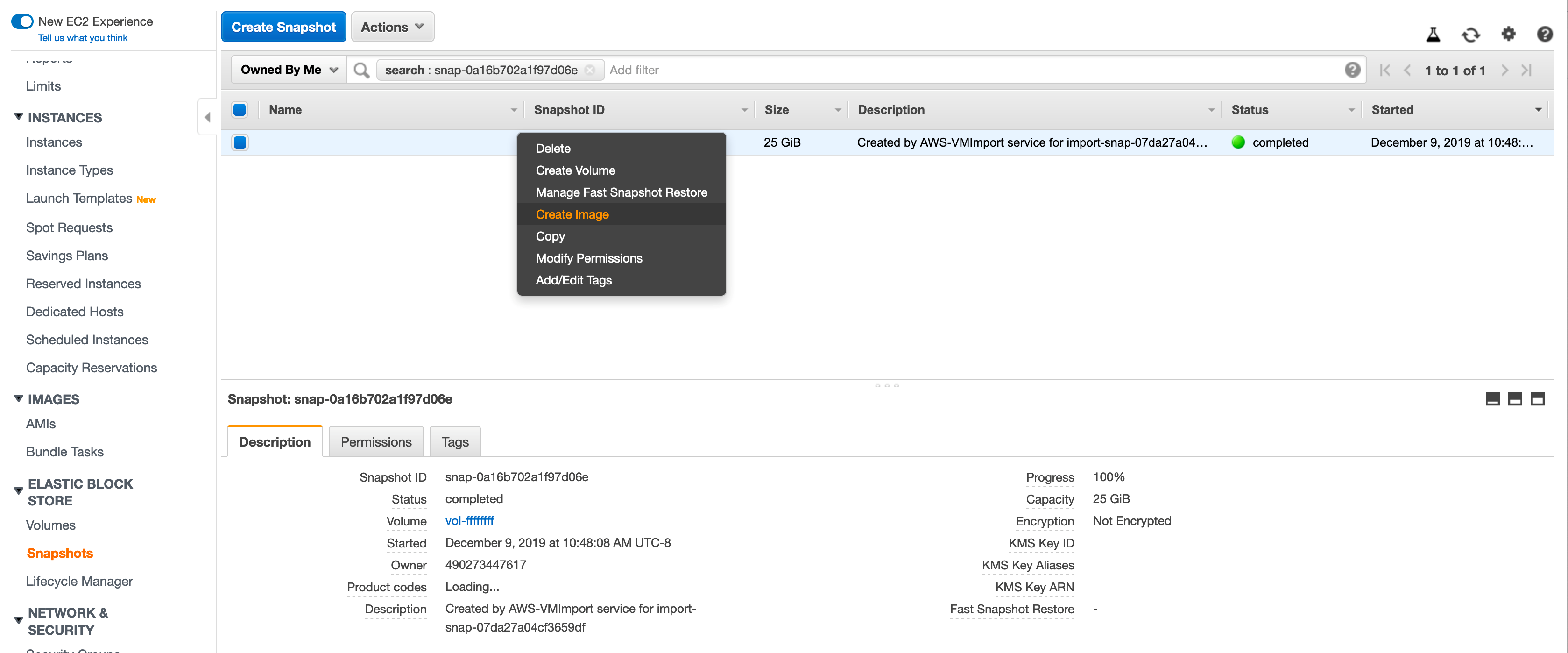
-
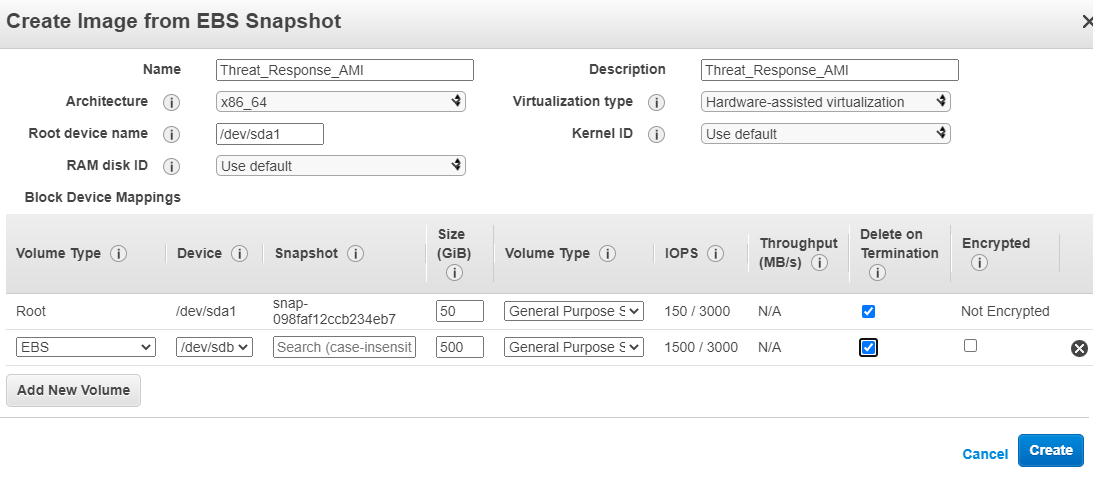
Specify a Name and Description.
-
Add another disk/volume to this image to accommodate the Threat Response/TRAP database.
Click on Add New Volume.
Keep the Volume Type as Amazon Elastic Block Store (EBS) and specify 500 GB of data storage (recommended).
Place a tick in the Delete on Termination box (if you wish) and then click on Create.
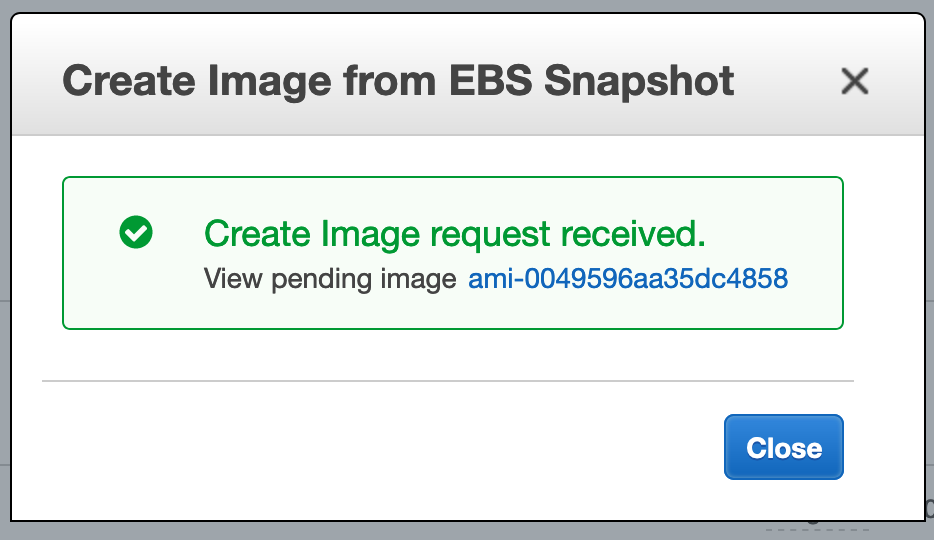
Note
An acknowledgement of receipt of the creation is displayed with the name of the image. (Clicking the link takes you to its listing.)
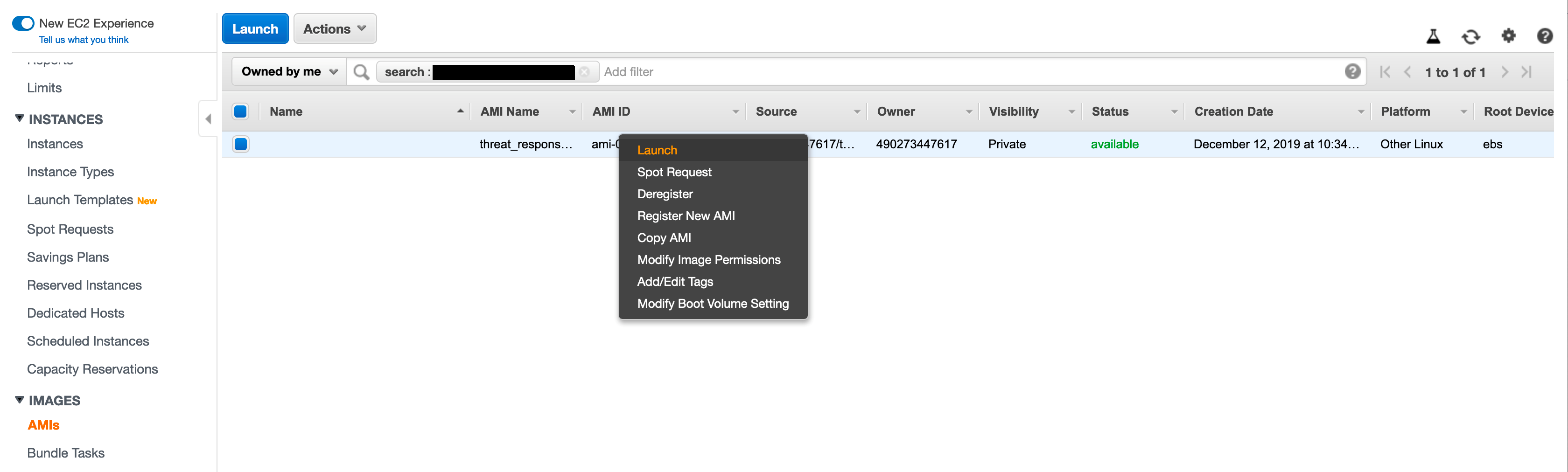
Launching the Threat Response AMI¶
-
Right click the listing for the AMI and then click on Launch.
-
Choose m5a.xlarge (minimum recommendation) for the Instance Type.
-
Configure the Instance details.
Be sure to set up the following items, as per instructions (for your AWS environment).
Network and Subnet (Virtual Private Cloud [VPC]);
AWS IAM Role;
Shutdown Behavior Set to “Stop”; and
Network Interfaces.
-
Add data storage. (Additional volume was already added when the AMI was created and therefore the process is complete.)
- Add “tags” if necessary.
-
Configure the Security Group. It is conditioned on your using
Inbound TCP by means of ports 22, 443, 8080;
Inbound UDP by means of port 514;
Outbound TCP by means of ports 22, 25, 443, 445, 389, 636; and
Oubound UDP by means of ports 53, 123, 137.
Refer to Required Ports for Network Communication for a complete list of required ports.
-
Review and then launch the new EC2 instance from the Threat Response AMI. Once it has been launched, note down the public IP address or the Elastic IP address, provided that one is set up.
Launching the Initial Configuration Wizard on Your Threat Response Instance¶
When trying to SSH to the instance as the ec2-user, you will need the private key file.
If you are using PuTTY to SSH to the instance, enter the IP address and port:
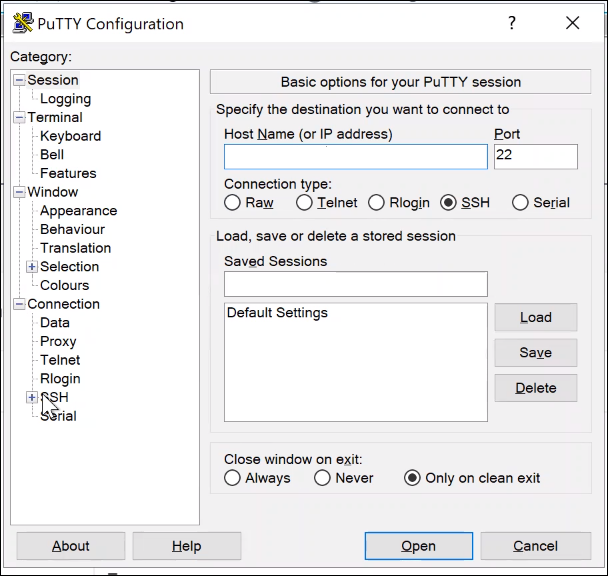
Then click on SSH > Auth > Private key file for authentication and locate the private key file you saved previously.
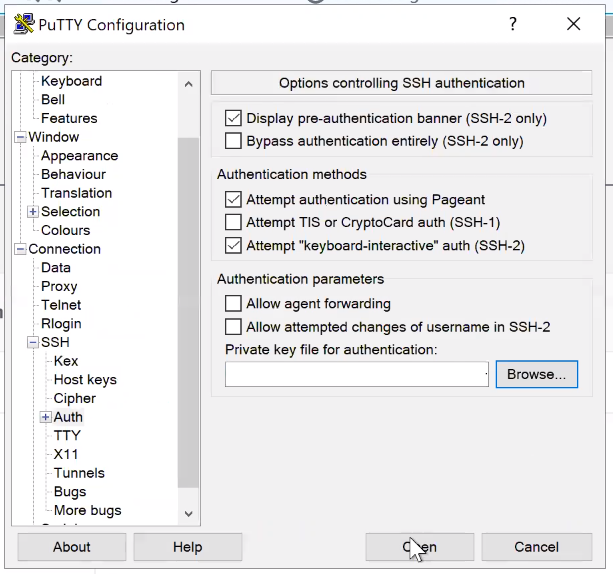
- SSH to the instance as an ec2-user.
- Run
sudo su - admin. This event triggers the Initial Configuration Wizard. - Specify the following information: admin password and Internal Docker subnet range (if these subnets conflict with a subnet on your internal network, otherwise accept the default).
Admin Password
a. Set an administrator password for your admin user.
b. Enter the password again for verification purposes.
Internal Docker Subnet Range
Threat Response uses the following two gateways/subnets for internal use by default:
- 172.31.250.1/24 is a subnet used by Docker containers running various back-end services in Threat Response.
- 172.31.251.1/24 is a subnet used by Docker containers created for scripted listeners, pollers, and responses.
Importantly, if they conflict with your network, you will not get return network traffic to any addresses within those ranges. If you choose Yes (to change the gateways), the following will appear. Note that the gateways must be different, unique subnets. Moreover, they are only meant to be routed within the appliance.
- Enter the gateway/subnet in CIDR format for Threat Response services, e.g. 172.31.250.1/24.
- Enter the gateway/subnet in CIDR format for Threat Response scripting services, e.g. 172.31.251.1/24.
You will be asked if you want to confirm the entirety of the settings above. Choose Yes to configure and initialize the system. This may take a few minutes.
Note
Importantly, these two /24 subnets have not been extracted from the existing network infrastructure. Note that you may pick two IP address ranges that do not overlap with anything else in your data center. Alternatively, you can pick Class C network IP address ranges (192.x.x.x).
Once the system is configured, the Threat Response UI will be accessible via https://ELASTIC_IP or https://PUBLIC_IP address.
License Installation¶
Use the steps in this section to install the Threat Response License.
- Open the Proofpoint Welcome email containing your license.
- Locate and copy the license key to use in step 7 below.
- In the browser window, enter
https://ptr_ip_address:8080. - Provide the Proofpoint
usernameandpasswordthen pressEnterto open the Proofpoint Appliance Management Console window. Use the hostname or Elastic IP address or Public IP address assigned to the Threat Response EC2 instance. - Click on
LicensingunderSystem Infoin the left-hand menu. - Paste the Proofpoint license key, copied from the Proofpoint “welcome” email in Step 2 above, into the field below Add New License.
- Click on Register a New License and then wait for the system to validate the license.
Note
If the Threat Response instance does not have network connectivity to Overcast (https://overcast.proofpoint.com/), you will be unable to validate the licenses on the system.
Note
Threat Response licenses have expiration dates. A month before your license expires, Threat Response opens a pop-up message each time you log in reminding that your license will expire soon. Once it expires, you will not be able to log in until you enter a new license in the Proofpoint Appliance Management console window. To renew your license, contact your Proofpoint Sales representative.
Logging Into Threat Response¶
Threat Response is the GUI tool associated with Threat Response. Use the steps in this section to run Threat Response in a browser window.
- Open a supported browser.
-
Navigate to to
https://ptr_ip_addressto open the Proofpoint Threat Response login window.This is the Elastic IP address or Public IP address assigned to the Threat Response instance in your AWS environment.
-
Enter your
usernameandpasswordinto Threat Response login window.This is the admin password you created for yourself when you set up the Threat Response instance in your AWS environment.
-
Click Login to open the Threat Response Dashboard window. Initially, this window will be empty of data.
Resetting the Administrative Password¶
Refer to Resetting the Administrative Password.
Configuring proxy settings¶
If a proxy is used on your network to access the Internet, use the steps below to configure Threat Response to use the proxy.
- Log in to Threat Response.
- Navigate to
System Settings>Appliance Configuration>Proxy Configuration. -
Configure Proxy settings…
- Check
Use proxy serverto enable the proxy - Host:
<proxy_ip_or_hostname> - Port:
<proxy_port>`` - Requires Authentication (Optional)
- Check
-
Click
Save Settings. - Click
Test Proxy Settingsto confirm that Internet routing works.
Defining internal networks¶
In order to properly determine attack direction, Threat Response needs to know which IP subnets are used on your network. Use the steps below to configure the Internal Networks on Threat Response.
- Log in to Threat Response.
- Navigate to
System Settings>Appliance Configuration>Local Networks. - Enter any public IP ranges used locally on your network into the User Defined Networks box. You should enter one entry per-line, and the list does support CIDR notation.
Note
The common, RFC 1918-defined private IP ranges are assigned as internal networks by default, and do not need to be entered into this list.
Upgrading Threat Response on AWS¶
Upgrading Threat Response running on AWS from an older version to a newer version requires a new instance to be set up and data migrated between the old and new instances. The upgrade process involves the following high-level steps:
Note
Be sure to disable any alert sources on the older version before you back up any data. Previously disabled alert sources can be enabled on the newer version after a successful restore operation.
-
Create a new instance using the VHDX file for the newer version. Refer to the instructions above on how to create this instance.
-
Perform a system backup from the old instance using an Amazon S3 bucket. Refer to the instructions in the Console Guide.
-
Download the master secret file from the old instance, by clicking on Download Master Secret File here, in the Appliance Management Console under Backups.
-
Upload this master secret file on the new instance, on the same page in the Appliance Management Console.
Warning
Uploading the master secret causes a restart of all the services. Please wait for the services to come back up before proceeding with next steps.
-
Restore the backed up data on the new instance from the same Amazon S3 bucket used in Step 2. Refer to the instructions in the Console Guide.
Important
Be sure to select Validate Encryption when restoring the backup on the new instance. Non-conformance can result in PTR/TRAP failing to communicate with other systems (mail servers, LDAP servers, TAP etc.).
Domain Controller Agent (DC agent)¶
The Threat Response DC Agent utilizes the domain controller’s event log to track user logins across the network. By monitoring the event log, the DC Agent can track the IPs from which users have logged in. This information is then relayed back to Threat Response, thus enabling Threat Response to associate usernames with security alerts that are received.
Step 1. Preparation for deployment¶
The Threat Response DC Agent references the domain controller’s record of user login events to build a list of user-to-IP mappings for Threat Response. Before installing the DC Agent, you must ensure that the domain controller is configured to record login events and that the DC Agent has the necessary access rights to read the domain controller’s event log.
Enable the Logon Audit in Active Directory¶
Audit logging must be enabled on your domain controller to successfully track logon events. These events are recorded in the domain controller’s event log where the DC Agent references them.
- Open the
Group Policy Managementconsole. - Locate the Domain Controllers organizational unit within your domain.
- Right-click
Domain Controllersand then selectCreate a GPO in this domain, and Link it here…:
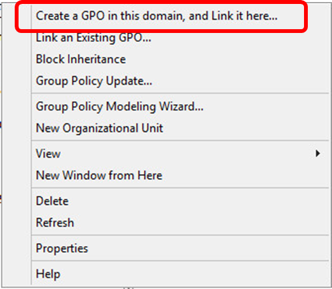
- Give the new GPO a name and then click on OK.
- Right-click the
new GPOand then selectEdit. - Navigate to
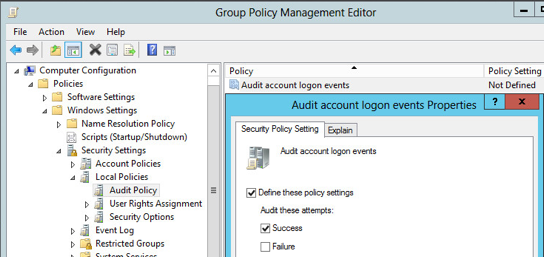
Computer Configuration>Policies>Windows Settings>Security Settings>Local Policies>Audit Policy. - Double-click
Audit account logon eventsto open thePropertieswindow. - Check off the box next to Success to enable the audit of successful logon attempts.
- Apply the changes.
Enable User-IP tracking in Threat Response¶
User-IP tracking must be enabled in Threat Response prior to installing the agent.
To enable user-IP tracking:
- Log in to Threat Response.
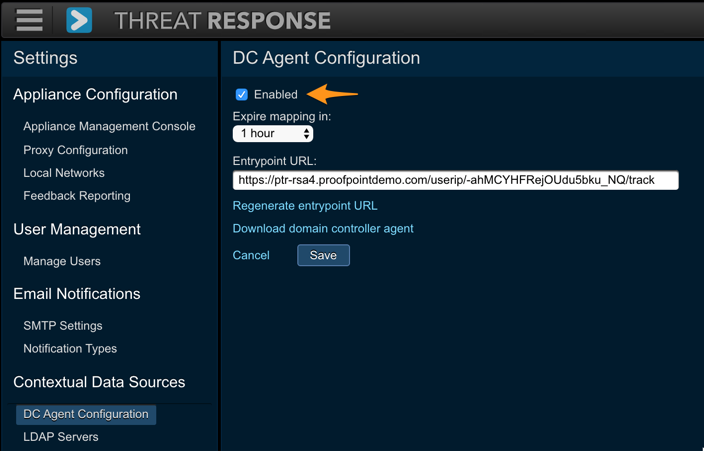
- Navigate to
System Settings>Contextual Data Sources>DC Agent Configuration. - Check off the box to enable User-IP Tracking.
- Save the changes.
Note
The Expire Mapping setting can be adjusted to specify the length of time that a username is associated with an IP address in Threat Response. The default is one hour.
Step 2. Domain Controller Agent installation¶
The Threat Response DC Agent needs to be installed so that it can access the event log for all the domain controllers used for user authentication. Two deployment options are available to install the DC Agent in your environment.
The table below compares the deployment options:
| Installation type | Characteristics |
|---|---|
| Direct Installation on DCs | - An instance must be installed on all the domain controllers |
| - Upgrades to the agent must be performed on each domain controller. | |
| Remote Installation | - A single instance of the DC Agent can remotely query multiple domain controllers. |
| - A service account is needed for the DC Agent. | |
| - Windows RPC must be enabled between the DC Agent and domain controller. | |
| Hybrid Installation | - A mixture of direct and remote installation is used. |
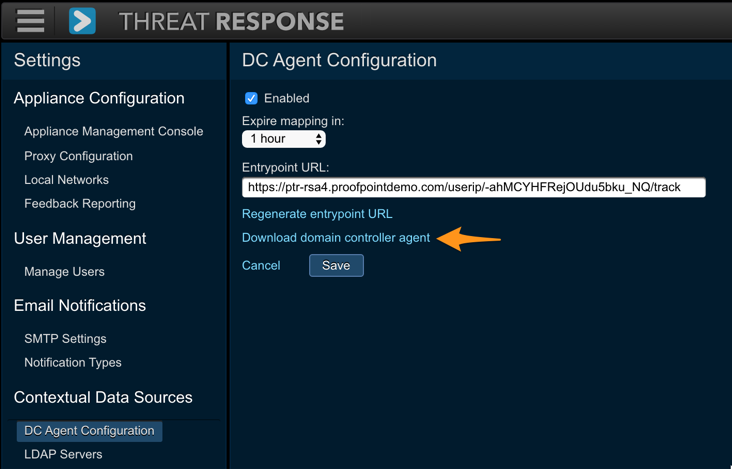
Download the DC Agent¶
The DC Agent can be downloaded directly from Threat Response. To download the agent, you can visit Threat Response from the machine onto which you are installing the agent or you can download it to your own system and then copy it to the other machine.
To download the DC Agent:
- Log in to Threat Response.
- Navigate to
System Settings>Contextual Data Sources>DC Agent Configuration. - Click on the link to Download Domain Controller Agent.
Note
Once DC agent is installed, you must copy and paste Threat Response’s unique Entrypoint URL to the DC Agent. While on the Data Collection page, click on Show Entrypoint URL… and copy the URL that is displayed. (It will be used in the next section.)
Install and Configure the DC Agent¶
With the agent downloaded and copied to the destination machine, you can now run the installer and complete the DC Agent configuration.
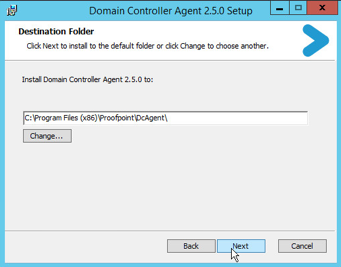
Installing the DC Agent:
- Double-click the DC Agent MSI package to begin the installation.
- Select the installation path and click on Next.
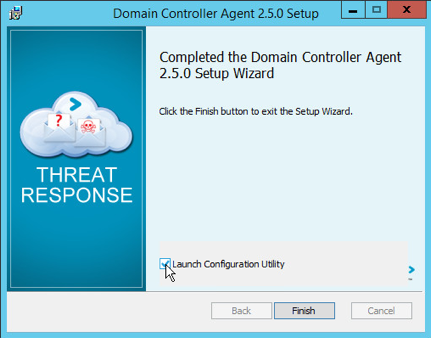
- Following the installation, click on the checkbox to Launch Configuration Utility and then click on Finish.
Step 3. Domain Controller Agent configuration¶
DC Agent Configuration Utility¶
The DC Agent configuration utility is used to specify the Threat Response systems with which the DC Agent will communicate. You must paste the Entrypoint URL (copied in ”Step 1”) into the DC Agent configuration.
To configure the DC Agent:
- Run the DC Agent configuration utility from Start Menu > Programs or run DcAgentSrv.exe from the installation directory.
- Click on the plus [+] button to add a new Threat Response instance to the configuration.
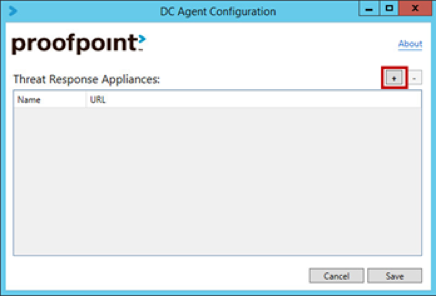
- Configure the following fields:
- Name: Provide a name for the appliance (a label to identify the system).
- URL: Paste the Entrypoint URL (from “Step 2”) into the URL field.
- Click on Save to save your changes and to close the configuration utility.
Remote configuration¶
If you are using the remote installation option rather than deploying directly on your domain controller, then you must complete the following additional steps after running the configuration utility.
Add the domain controllers to the DC Agent configuration file:
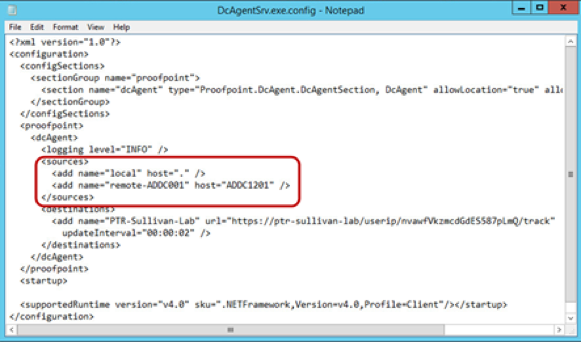
- Run Notepad as an administrator and open the DC Agent configuration file.
- 32-bit OS: C:\Program Files\Proofpoint\DcAgent\DcAgentSrv.exe.config
- 64-bit OS: C:\Program Files (x86)\Proofpoint\DcAgent\DcAgentSrv.exe.config
- Locate the
<sources>tag in the configuration file. - Create new entries below the
<sources>tag for each of your domain controllers.
Example: <add name="dc-01" host="dc01.example.com"/>Note
You should create an entry for each domain controller against which users authenticate. Note that the “host” value must be able to be resolved and routed from the system hosting the DC Agent.
- Save the file and exit Notepad.
As a next step you need to create a service account for the DC Agent:
- Create a service account in Active Directory for the DC Agent.
- Add this account to the Event Log Readers group in Active Directory. This enables the agent to remotely access the event logs on the domain controllers.
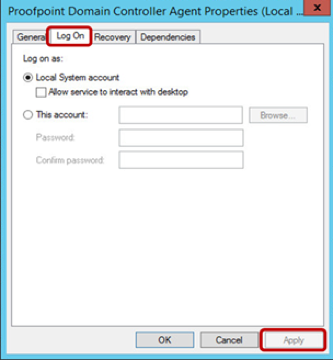
- Configure the DC Agent service to run as the service account.
- Open the Services console in Windows.
- Right-click the Proofpoint Domain Controller Agent service and then select Properties.
- In the Log On tab, set the DC Agent service to run as your service account.
- Click on Apply to save your changes.
Step 4. Domain Controller Agent restart¶
With the configuration in place, it is advisable to restart the DC Agent service to ensure that no warnings are recorded in the server’s event logs.
To restart the DC Agent service:
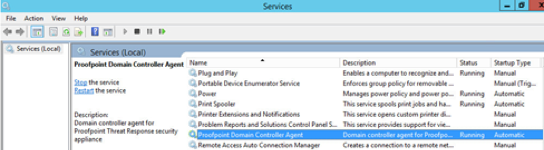
- Open the Services administrative console in Windows and locate the Proofpoint Domain Controller Agent service.
- Click on Restart to restart the service.
To confirm that the service started successfully:
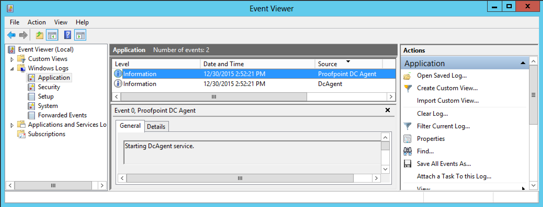
- Open the Windows Event Viewer.
- Navigate to Windows Logs > Application.
- Review Proofpoint DC Agent entries for successful startup events.
With the service successfully started, Threat Response begins receiving user-to-IP mappings from the DC Agent and associate usernames with the alerts that it receives.
Reviewing the Event Viewer for Startup Warnings¶
If any warnings are shown in the Event Viewer, they should be reviewed to determine the cause.
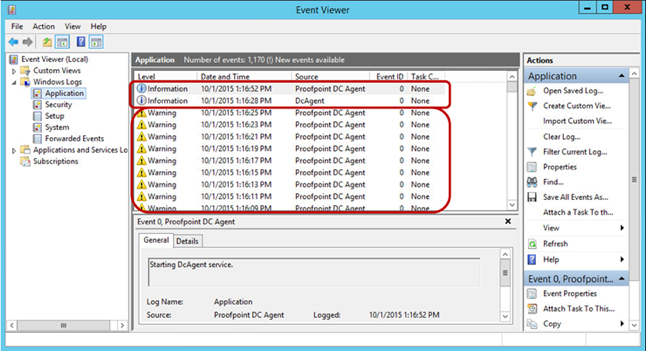
Warnings can be generated for a number of reasons. They are typically seen when the DC Agent is either unable to reach Threat Response or is unable to connect to the domain controllers (in a remote configuration). To settle connectivity issues, ensure that the system running the DC Agent can resolve any hostnames used in the configuration. Furthermore, confirm that any firewalls between the systems are configured to allow this traffic to pass.
The DC Agent uses HTTPS to communicate with Threat Response. You can quickly confirm connectivity to Threat Response by opening a browser and connecting to the Entrypoint URL from “Step 1.” In the DC Agent’s remote configuration, it uses Windows RPC to query the domain controllers.
Active Directory and LDAP¶
LDAP / Active Directory support enables Threat Response to map users to alerts that it receives, and to retrieve details about user accounts, such as location and group membership. The configuration is broken up into the two sections below.
Note
To get started, DomainUser is the only required privilege for your LDAP service account for user alert enrichment. For Active Directory Responses (password resets, account disables etc) an AccountOperators role or equivalent is required.
Server Configuration¶
Create a server listing in Threat Response to tell the systems which LDAP server to query for user information. Multiple servers can be created.
- Log in to Threat Response.
- Navigate to
System Settings>Contextual Data Sources>LDAP Servers. - Click the blue Add (+) button next to LDAP Servers to bring up the New LDAP Server panel.
- Set the following fields:
- IP/Hostname:
<ldap_hostname_or_ip> - Port:
<ldap_port> - SSL: Check to enable SSL encryption
- Search Base:
<directory_path>(e.g., DC=domain,DC=com) - Requires Authentication
- IP/Hostname:
- Save changes.
Note
The authentication username may vary in syntax depending on your directory server’s authentication requirements. In most cases, the full, distinguished name (DN) for the user should be used as the username.
LDAP attribute selection¶
Threat Response allows you to configure the user attributes that will be pulled from your LDAP / Active Directory server. By default, the system is configured to collect and display the following common user attributes:
- Display Name
- Telephone Number
- Mobile Number
- Email Address
- Company
- Department
- Street Address
- City
- State
- Country
- Group Memberships
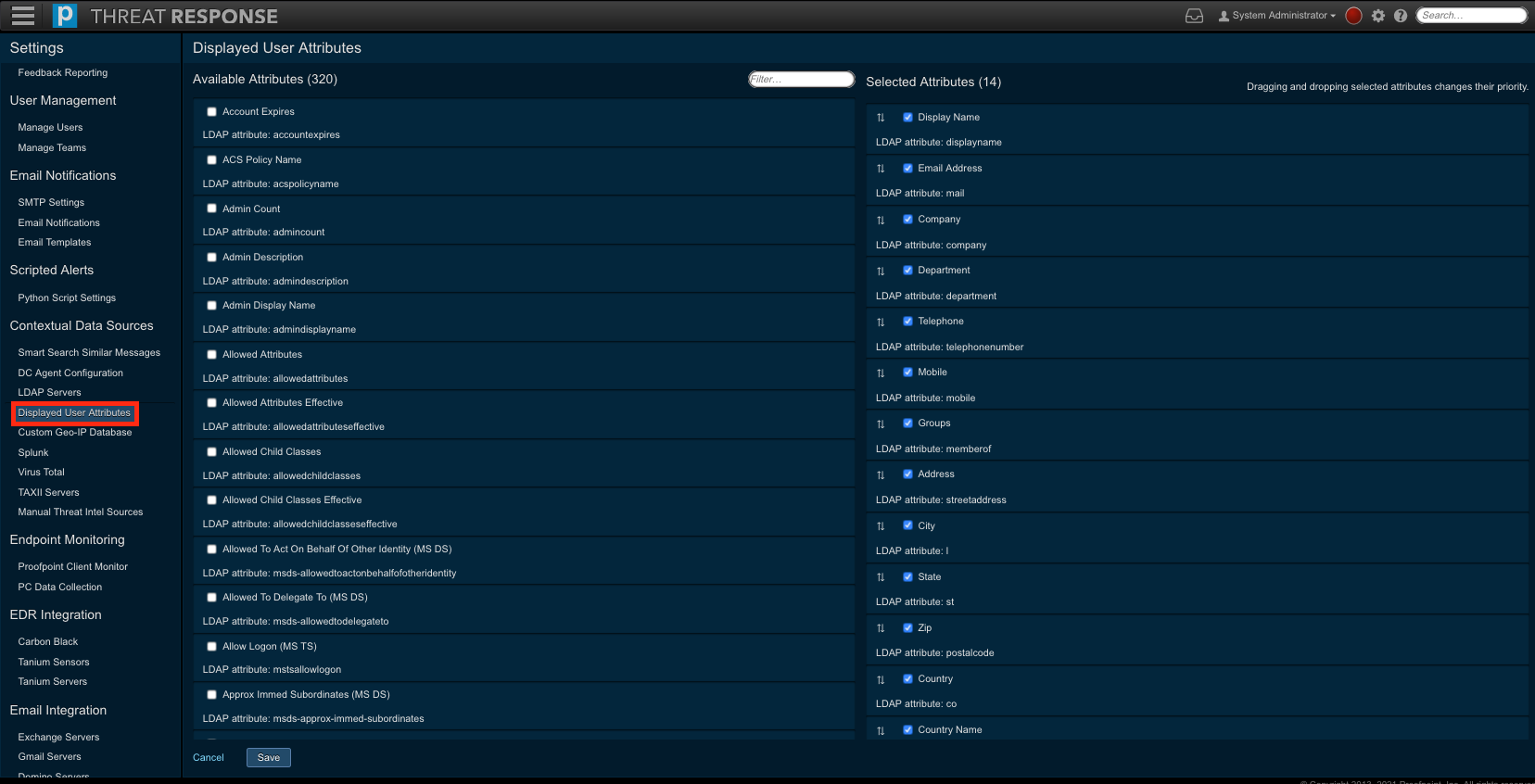
To add, or remove items from this list, use the steps below.
- Log in to Threat Response.
- Navigate to
Settings>Contextual Data Sources>Displayed User Attributes. - Select attribute that you would like to be displayed for users.
- Place a checkmark next to items in
Available Attributesto select them - Uncheck items in Selected Attributes to remove them
- Place a checkmark next to items in
- Re-order the Selected Attributes by dragging-and-dropping items into your preferred order. This is how they will be displayed in the UI.
- Click Save Settings.